
Short Bytes: A group of researchers has revealed a new method to steal sensitive information from a user’s computer or phone. Named WindTalker, this technique sniffs a user’s hand movement on the screen and keyboard by reading the channel state information (CSI). To block this attack, the payment apps can simply randomize the keypad layouts.
very other day, we come across different developments in the world of communication and risks associated with the existing technologies. Back in August, we read how your Wi-Fi can spy on you and actually “see” a person present in the room. In another recent development, a group of researchers has developed WindTalker.
WindTalker uses the fact that the modern Wi-Fi also imprints some of our finger movements, swipes, passwords, and PINs on the radio signal. This has been demonstrated by a group of researchers from the Shanghai Jaio Tong University, the University of Massachusetts at Boston, and the University of South Florida.
The research paper published by them has been named When CSI Meets Public WiFi: Inferring Your Mobile Phone Password via WiFi Signals, where “CSI” means “channel state information”.
The method used by these researchers uses the modern Multiple-Input, Multiple-Output (MIMO) antenna configurations. In these Wi-Fi routers, the controller software uses small phase differences between the antennas to cancel or reinforce signals in different directions, The Register writes. So, WindTalker won’t work if you have a vintage router.
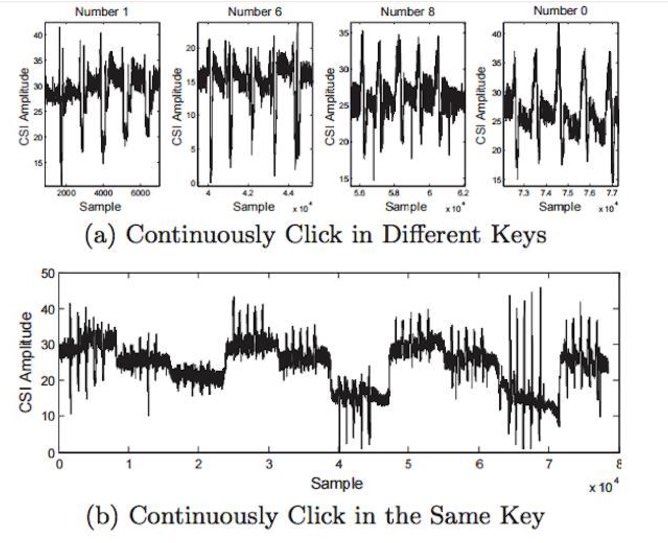
The kit designed by the researchers records very small changes in the signal, including those from the state variations due to the user’s hand movements during screen input. Different hand movements and finger movements introduce a unique interference in the signals, which is reflected by the channel state information.
Moreover, to carry out this attack, one doesn’t need to compromise the target. The attacker can steal the passwords with the help of a malicious Wi-Fi hotspot. Here’s a picture of CSI values of a user repeatedly clicks on the same button.
The researchers suggest a simple way to block WindTalker attacks. In their paper, they write that simply randomizing the keypad layouts will solve the problem. For detailed information, you can find the research paper here.
Did you find this article helpful? Don’t forget to drop your feedback in the comments section below.
Comments
Post a Comment